2024-07-12
한어Русский языкEnglishFrançaisIndonesianSanskrit日本語DeutschPortuguêsΕλληνικάespañolItalianoSuomalainenLatina
When you want to stay private or anonymous on the Internet, the first thing you should do is hide your IP address. Your IP address can easily be traced back to you and used to learn your location. The following article will teach you how to hide yourself from anyone trying to track your activities.

First, let's discuss a little bit what an IP address is.
What you need to know is that every time you connect to the internet, it is a unique number assigned to your computer by your Internet Service Provider.
This means that no two people have the same IP address, and if someone wants to find out who you are or where you live, it is likely that your IP address can be traced back to you.
In fact, just by reading an article like this one on your laptop or smartphone, the platform can track your IP address and know where you are.
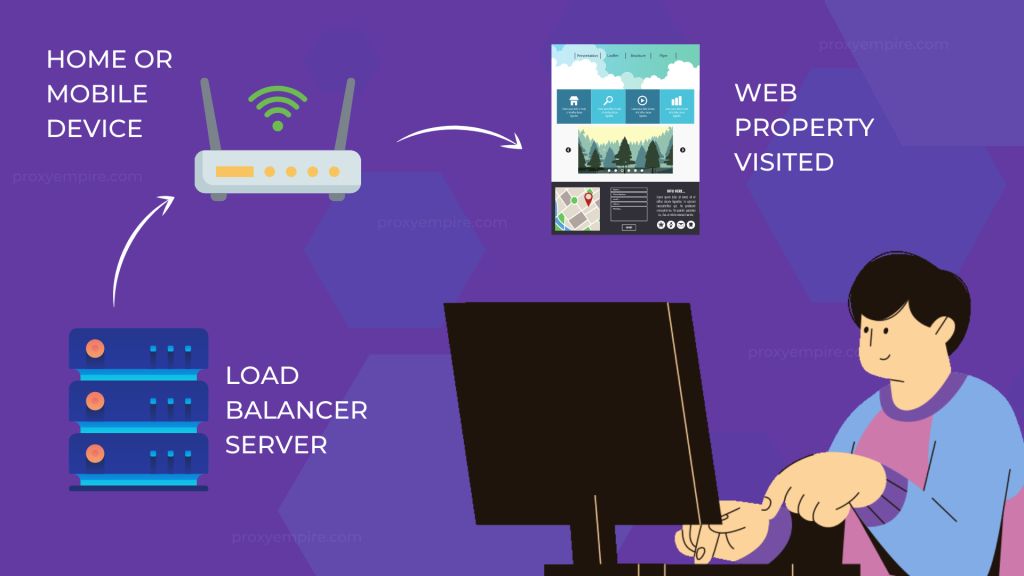
A proxy by definition is just an object between you and the platform you are connecting to. They work by assigning you an IP address from your real Internet Service Provider or mobile proxy (phone carrier).
Unlike free proxies that reveal your real IP address, reverse proxy does not reveal your information to the web resources you visit.
As with any technology, it’s important to choose a reliable proxy like IPFoxy that keeps no logs, accepts payments that respect privacy, and is 100% legal to access people’s devices.
Datacenter-sourced proxies come from large server warehouses available only in major cities, whereas residential and mobile proxies (reverse connections) are widely spread around the world because they come from real devices.
Finally, to get the most out of your proxy, you should use anti-detection software or split browser profiles to separate your browser fingerprint.
A virtual external server reroutes all of your internet traffic so that other people don't see your computer's IP address, but instead see the address of the server you're passing through.
The idea is to encrypt all of your data, so if someone is trying to track your internet connection, they'll have a hard time doing it.
Another method is called TOR, or The Onion Router. What it does is bounce your connection through multiple machines so that it can't be traced back to you, but instead it bounces around until there are too many traces to follow.
When you use TOR, your IP address is hidden through "onion routing," a method where data packets are sent through a network of relays before reaching their destination.
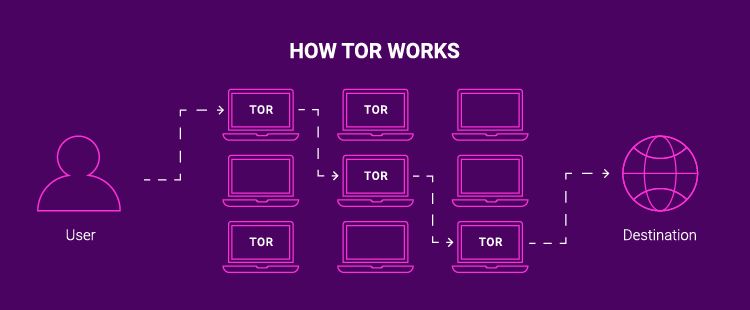
When this happens, someone trying to trace it will only get partial data because it has changed so many times before reaching the final connection point.
You can increase your anonymity by installing and using the TOR browser.
What you need to know is that TOR can be slow at times, but it is usually worth the wait when you are seeking absolute privacy and anonymity on the Internet. Web platforms can also know that you are using TOR and block your connection.
Now you have three effective ways to protect your personal and business life from prying eyes. I hope you found this explanatory text helpful.