2024-07-12
한어Русский языкEnglishFrançaisIndonesianSanskrit日本語DeutschPortuguêsΕλληνικάespañolItalianoSuomalainenLatina
K8s offline deployment

k8s offline deployment
Ad singula, vide articulum: "Online institutionem de dock and offline packaging of back-finis projects"
https://blog.csdn.net/qq_45371023/article/details/140279746?spm=1001.2014.3001.5501
All files used are at:
Link: https://pan.baidu.com/s/10cb-dXkgdShdjPEBCyvTrw?pwd=fpuy
Extraction codice: fpuy
Install cri_dockerd 1.
rpm -ivh cri-dockerd-0.3.9-3.el8.x86_64.rpm

2. Reload systema daemonis → Pone cri-dockerd incipere automatice → Committitur cri-dockerd
Reload ratio daemonis
sudo systemctl daemon-reload
Set cri-dckerd incipere automatice
sudo systemctl enable cri-docker.socket cri-docker
Satus cri-dockerd
sudo systemctl start cri-docker.socket cri-docker
sudo systemctl status cri-docker.socket
sudo systemctl status cri-docker
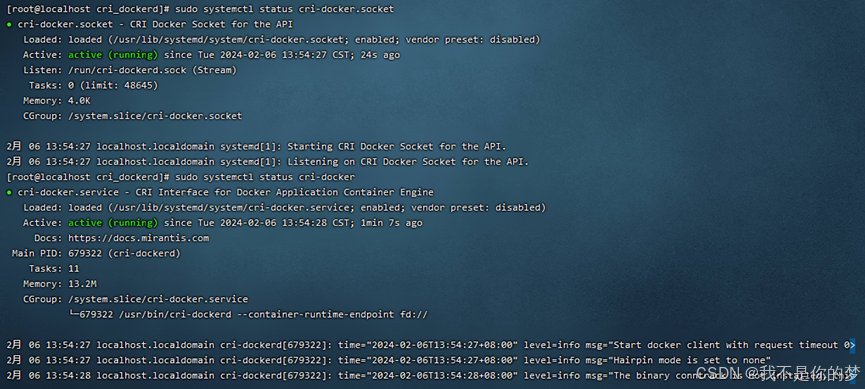
Quaestio: Deficio incipere cri-Docker
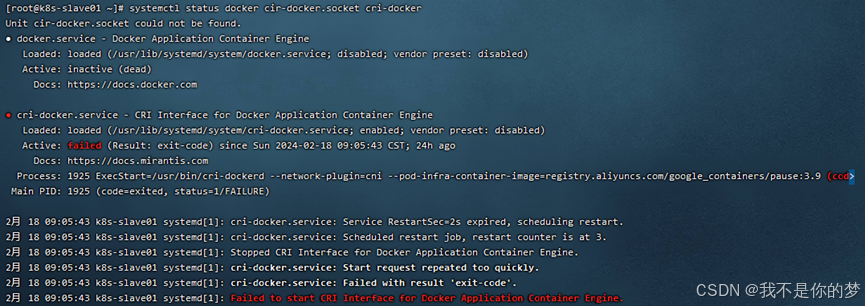
mensura;
Modus I: systemctl sileo docker # Sileo docker
Modus II: Docke Uninstall et restituo eam, et rursus gradus superiores praestare
1. Install kubectl
sudo install -o root -g root -m 0755 kubectl /usr/local/bin/kubectl
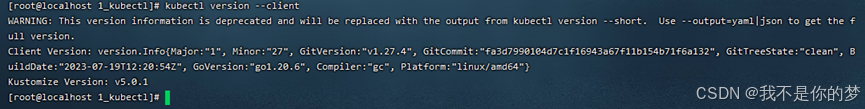
2. Reprehendo institutionem sive completum est
kubectl version --client
3. Aperi portum vel claudere firewall (ut lenis processus institutionem)
Apertum portum (server nubem)
Apertum portum 6443
sudo firewall-cmd --zone=public --add-port=6443/tcp --permanent
Reload firewall
sudo firewall-cmd --reload
Omnes patentes portus
sudo firewall-cmd --zone=public --list-ports
Aut averte firewall (machina virtual)
Illuminationes firewall
sudo systemctl stop firewalld
Firewall declinemus auto- initium
sudo systemctl disable firewalld
4. inactivare SELinux (ut possit accedere ratio continentis facultates)
sudo setenforce 0
sudo sed -i 's/^SELINUX=enforcing$/SELINUX=permissive/' /etc/selinux/config
5. Instrue kubeadm, kubelet et kubectl
Download pertinet ad sarcinam institutionis offline in rpm forma, quae sub 3_yum_package exstat.
cd 3_yum_package && rpm -ivh *.rpm
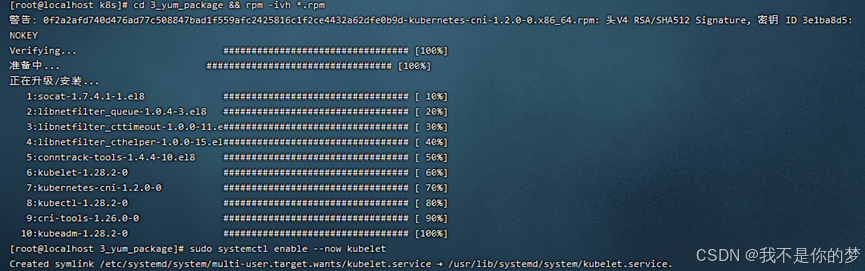
6. Set kubelet incipere automatice
sudo systemctl enable --now kubelet
His gradibus supra peractis, sequenti ambitu habebis
·Duo servientes vel machinis virtualis cum diversis IP inscriptionibus communicare possunt inter se et statum LAN conservare.34 et 192,168..35
· Continens runtime (Docker+cri_dockerd) in utroque ministris inauguratus est, et kubernetes componentium kubectl, kubeadm et kubelet inaugurati sunt.
7. Claude permutatio partitio. Haec clausula in clausuram temporalem et clausuram perpetua divisa commendatur pro ambitus machinae virtualis, quia saepe in et off convertetur.
PERMUTO tempus claudere maceriam
swapoff -a
PERMUTO maceriam claudere, lineam quae permuto in fstab explanare.
vi /etc/fstab
# /dev/mapper/centos-VERTO PERMUTO defaltis 0 0
Sileo ut effectum sortiatur. Restarting statum cri-dockerd mutare potest cri-dockerd et incipit cri-dockerd ut cri -dockerd status est normalis
reboot
8. Install runc ut k8s operating elit
install runc
sudo install -m 755 runc.amd64 /usr/local/bin/runc
# Reprehendo si institutionem est felix
runc -v

9. Docker et cri-dockerd accelerationem imaginis domesticae statuit (Cum nomina sequentium fasciculorum programmatum in hoc folder utendum habeant inscriptiones Speculum habent, commendatur speculi accelerationem correspondentem configurare etiam in network locali area, ne kubectl ab Interreti requirat ad trahere fasciculos programmales et post speculum locale neglecto. institutionem absolvit.)
sudo tee /etc/docker/daemon.json <<-'EOF'
{
"registry-mirrors": ["https://tsvqojsz.mirror.aliyuncs.com"]
}
EOF
# 找到第10行
vi /usr/lib/systemd/system/cri-docker.service
# 修改为ExecStart=/usr/bin/cri-dockerd --network-plugin=cni --pod-infra-container-image=registry.aliyuncs.com/google_containers/pause:3.9
Sileo Docker components
systemctl daemon-reload && systemctl restart docker cri-docker.socket cri-docker
# Reprehendo Docker componentia status
systemctl status docker cir-docker.socket cri-docker
10. Reprehendo hostname et exercituum
dominus nodi
hostname est k8s-dominum
vi /etc/hostname
Addere domain nomen tabularum faciendarum
echo "192.168.**.35 k8s-slave01">> /etc/hosts
Alii lymphaticorum
hostname为k8s-slave01
vi /etc/hostname
Addere domain nomen tabularum faciendarum
echo "192.168.**.34 k8s-master" >> /etc/hosts
11. Transeamus IPv4 et videant iptables pontis fluere
cat <<EOF | sudo tee /etc/modules-load.d/k8s.conf
overlay
br_netfilter
EOF
sudo modprobe overlay
sudo modprobe br_netfilter
Pone parametri sysctl requisiti, qui per reboots perseverant
cat <<EOF | sudo tee /etc/sysctl.d/k8s.conf
net.bridge.bridge-nf-call-iptables = 1
net.bridge.bridge-nf-call-ip6tables = 1
net.ipv4.ip_forward = 1
EOF
#Apply sysctl parametri sine restarting
sudo sysctl --system
lsmod | grep br_netfilter
lsmod | grep overlay
sysctl net.bridge.bridge-nf-call-iptables net.bridge.bridge-nf-call-ip6tables net.ipv4.ip_forward
# Iptables si error adhuc per init, quaeso exequi
echo "1">/proc/sys/net/bridge/bridge-nf-call-iptables
echo "1">/proc/sys/net/ipv4/ip_forward
12. Initialize dominus nodi
Priusquam initializationem obtinere debes imaginem docularium requisitam ad initializationem per imagines config kubeadm:
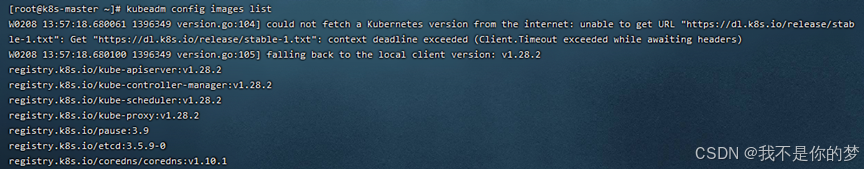
Instrue imaginem docker onus -i **. tar
Files imaginum pertinentes in 5_kubeadm-images existunt.
Praestare initialization:
kubeadm init --node-name=k8s-master list--image-repository=registry.aliyuncs.com/google_containers --cri-socket=unix:///var/run/cri-dockerd.sock --apiserver-advertise-address=192.168.**.34 --pod-network-cidr=10.244.0.0/16 --service-cidr=10.96.0.0/12
-image-repository=registry.aliyuncs.com/google_containers # Repone receptaculum imaginis receptaculum cum Alibaba Cloud. Alioquin imaginis ob rationes retis detrahi non potest, et exsecutio certe deficient.
-cri-socket=unix:///var/run/cri-dockerd.sock # Hic est continens runtime definitum, quia continens etiam unum ex componentibus Docker detegit plures ambitus currendi continens esse, unum manuale eligere debet. Hic etiam videri potest quod continens actu multo levius sit quam Docker.
-apiserver-advertise-electronica=192.168.56.50 # Pone sparsim pro API servo. Locum IPv4 elige hic.
-pod-network-cidr=10.244.0.0/16 # Specificare electronicae IP range, quae adhiberi potest a retis vasculi.
-service-cidr=10.96.0.0/12 # Specificare portionem additam IP oratio pro virtuali IP inscriptione servitii.
Problem: cordns:v1.10.1 ceptum non est, re vera cordns: v1.10.1 iam existit, sed est cordns: 1.10.1.
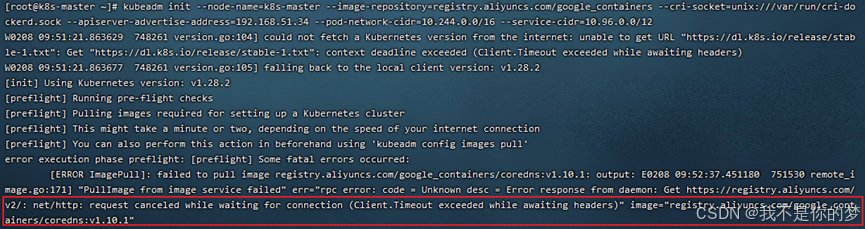
Mensurae: Modify tag cordns.
docker tag registry.aliyuncs.com/google_containers/coredns:1.10.1 registry.aliyuncs.com/google_containers/coredns:v1.10.1
Re- faciendam initialization mandatum
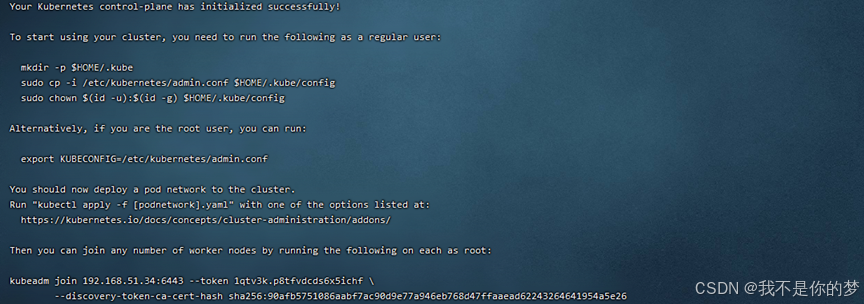
Adnotare informationes infra kubeadm iungere, quae pro nodi iungere requiritur.
kubeadm join 192.168.51.34:6443 --token 1qtv3k.p8tfvdcds6x5ichf
--discovery-token-ca-cert-hash sha256:90afb5751086aabf7ac90d9e77a946eb768d47ffaaead62243264641954a5e26
Si oblitus es, tessera kubeadm uti potes ad interrogationem. Vestigium exsistit per 24 horas, signum re-creare kubeadm creare -- print-iungere-mandatum et delere utens kubeadm tessera signum delete signum.
Non-radix users placet facere
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
Radix usor directe
Temporale effectum obtinet et irrita fiet post restarting.
export KUBECONFIG=/etc/kubernetes/admin.conf
Effectum perpetuum obtinet. Non opus est hoc mandatum exequi iterum postquam kubeadm reset et iterum init.
echo "export KUBECONFIG=/etc/kubernetes/admin.conf" >> ~/.bash_profile
Post exsecutionem mandatorum permanentem efficacissimum, debes fontem efficacem efficere.
source ~/.bash_profile
Reprehendo an configuratione est effective
echo $KUBECONFIG
/etc/kubernetes/admin.conf
13. Install ac configurare network obturaculum-ins
Flannel hic adhibetur ad plicandum et fasciculum kube-flannel.yml ad servo.
Servo ad imaginem pertinet ad institutionem upload. kube-flannel.yml et imaginum imaginum in 6_kube-flannel exstant.
Query network card
ifconfig
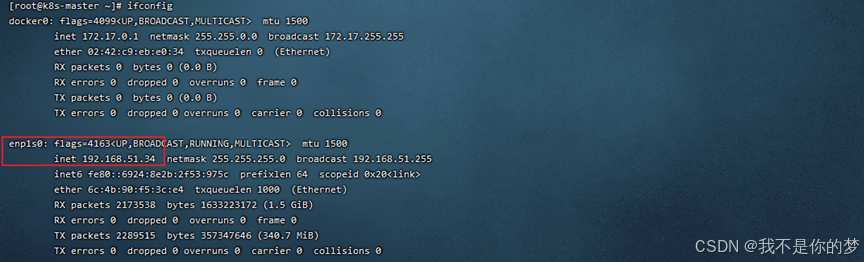
kube-flannel.yml card retis enp1s0 per defaltam exspectabit. In hoc exemplo, 34 card retis enp1s0 est et mutari non debet.
//Modify kube-flannel.yml ex 35 et adde -iface=enp0s3 ut definias (enp0s3 hic est card retis ipsi ip respondens, qualis pars in capsula supra). Loci parametri sunt hoc modo:
container:
......
command:
- /opt/bin/flanneld
arg:
- --ip-masq
- --kube-subnet-mgr
- --iface=enp4s0
Configurans flannel retis plugin pro Kubernetes
kubectl apply -f /data/k8s/6_kube-flannel/kube-flannel.yml
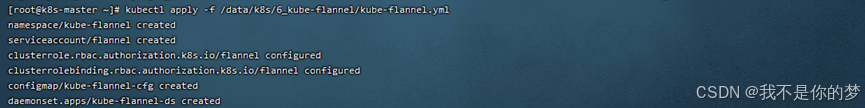
cat /run/flannel/subnet.env
# Si fasciculus talis vel folder non est, necesse est ut illud manually conficiat.
FLANNEL_NETWORK=10.244.0.0/16
FLANNEL_SUBNET=10.244.0.1/24
FLANNEL_MTU=1450
FLANNEL_IPMASQ=true
14. Nodus nodi coniungit Master .
14.1.
scp /etc/kubernetes/admin.conf 192.168.56.51:/etc/kubernetes/
# Noli oblivisci addere admin.conf ambitu variabili.
echo "export KUBECONFIG=/etc/kubernetes/admin.conf" >> ~/.bash_profile
source ~/.bash_profile
Difficultas si exscribend testatem:
ECDSA clavem militiae ad 192.168.55.187 mutavit et postulasti stricte recognitionem.Host clavem verificationis defecit.
Facere sequentia reficere
ssh-keygen -R 192.168.55.187
14.2.
Exempli gratia:
kubeadm iungere 192.168.51.34:6443 -- token by7t4x.da3f98dzrvjylykz
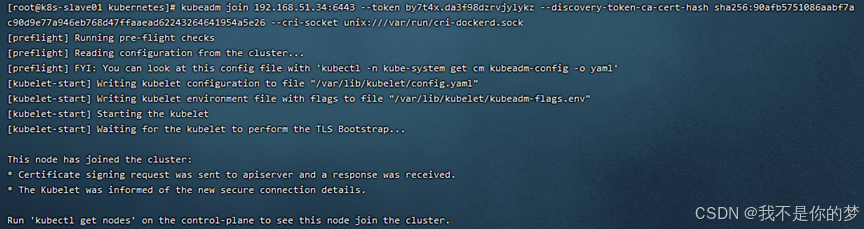
14.3.

Botrus k8s feliciter instruxit! ! !
kubectl adepto lymphaticorum
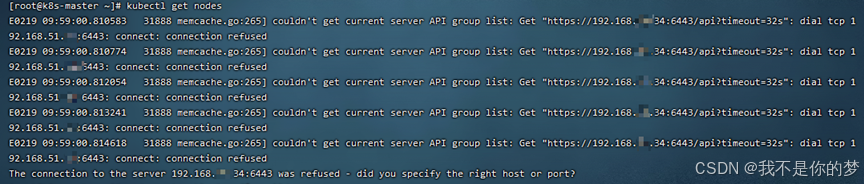
Mensurae: Perscriptio num clausus PERMUTO; reprehendo utrum firewall portum aperiat 6443
Close VERTO
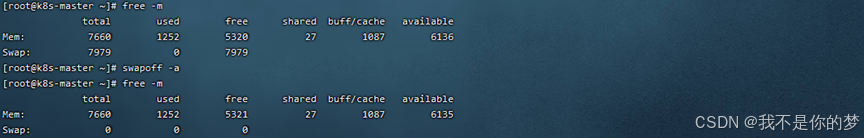
Ad tempus averte firewall

success

kubectl adepto lymphaticorum
His additis nodi k8s ad botrum, reprehendo statum nodi notReady esse.

mensura;
systemctl restart kubelet.service
systemctl restart docker.service
Sileo kubelet et docker

kubeadm iungere 192.168.51.34:6443 -- token l2qlvh.and3fnjmzecueu9h
Timeout initialization occurrit cum nodis infantis additis ad botrum k8s.
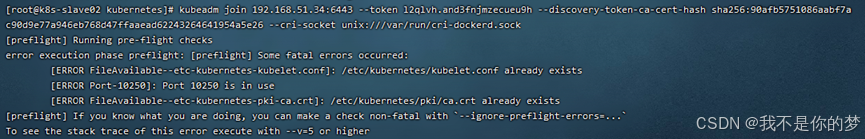
mensura;
kubeadm reset -f --cri-socket unix:///var/run/cri-dockerd.sock
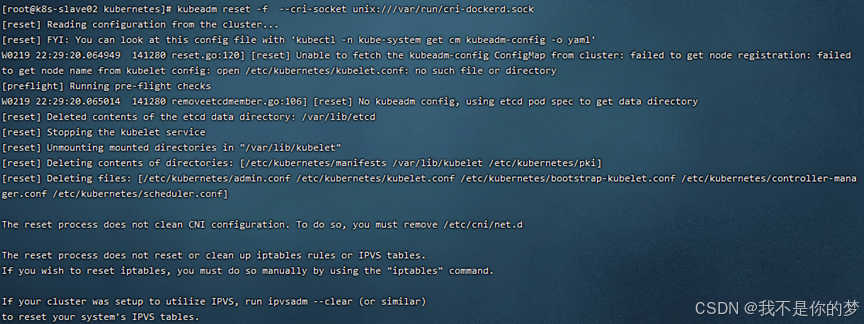
success
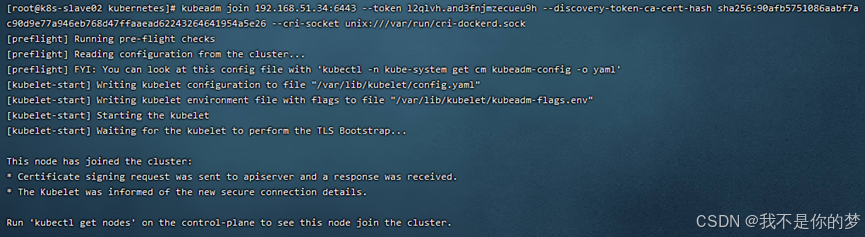

Exemplar /etc/kubernetes/admin.conf in machina nodi magistri ad machinam nodi servi
scp /etc/kubernetes/admin.conf 192.168.55.187:/etc/kubernetes/
Si tabella exscribenda deficit, error nuntius talis est:
ECDSA clavem militiae pro 192.168.55.187 mutavit et stricte reprehensionem postulasti.
Defecit verificationem clavis exercitum.
Facere sequentia reficere
ssh-keygen -R 192.168.55.187
kubectl delete node k8s-slave01
kubectl delete node k8s-slave02
kubectl delete node k8s-master
servus nodi
rm -rf /etc/kubernetes/*
kubeadm reset --cri-socket unix:///var/run/cri-dockerd.sock
dominus nodi
rm -rf /etc/kubernetes/*
rm -rf ~/.kube/*
rm -rf /var/lib/etcd/*
kubeadm reset -f --cri-socket unix:///var/run/cri-dockerd.sock
Si opus est, botrum innovare k8s.
kubeadm init --node-name=k8s-master --image-repository=registry.aliyuncs.com/google_containers --cri-socket=unix:///var/run/cri-dockerd.sock --apiserver-advertise-address=192.168.51.34 --pod-network-cidr=10.244.0.0/16 --service-cidr=10.96.0.0/12
dominus nodi
kubectl apply -f /data/k8s/6_kube-flannel/kube-flannel.yml
kubectl get pod -A
dominus nodi
scp /etc/kubernetes/admin.conf 192.168.51.35:/etc/kubernetes/
scp /etc/kubernetes/admin.conf 192.168.51.36:/etc/kubernetes/
servus nodi
kubeadm join 192.168.51.34:6443 --token 1k9kdy.dvn2qbtd7rjar1ly
--discovery-token-ca-cert-hash sha256:ff90d8ed41ae1902a839194f179a1c3ba8374a5197ea3111e10e5ca1c09fa442 --cri-socket unix:///var/run/cri-dockerd.sock
kubectl get pod -A
kubectl get nodes