2024-07-12
한어Русский языкEnglishFrançaisIndonesianSanskrit日本語DeutschPortuguêsΕλληνικάespañolItalianoSuomalainenLatina
Secondary injection vulnerability is a kind of security vulnerability that is widely found in Web applications. Compared with primary injection vulnerability, secondary injection vulnerability is more difficult to detect, but it has the same attack power as primary injection attack vulnerability.
Hackers construct data and submit HTTP data message requests in browsers or other software to the server for processing. The submitted data message requests may contain SQL statements or commands constructed by hackers.
The server-side application will store the data information submitted by the hacker, usually in a database. The main purpose of the stored data information is to provide original input data for the application to perform other functions and respond to client requests.
The hacker sends a second request data message to the server that is different from the first one.
After the server receives the second request information submitted by the hacker, in order to process the request, the server will query the data information already stored in the database and process it, resulting in the SQL statement or command constructed by the hacker in the first request being executed in the server environment.
The server returns the result data of the execution. The hacker can use the returned result data to determine whether the secondary injection vulnerability is successfully exploited.
In summary, secondary injection is caused by not filtering the data when it is stored in the database. First, a constructed special character request is submitted and stored in the database. Then, when the second request is submitted, it interacts with the characters submitted to the database for the first time, forming a new SQL statement that is executed. Take the 24th level of sqli-labs as an example
sqli-labs less-24
1. Click Register User as follows

The registered user name here is admin'#

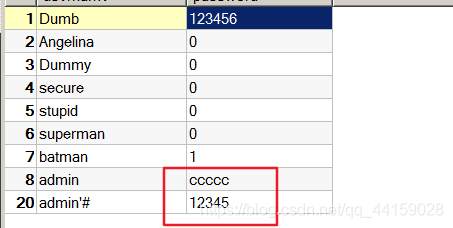
At this point we check the database, the registered users have been stored, and the admin password is DDD

2. Log in to the registered account and change the password to ccccc

At this point, it prompts that the password has been successfully changed
At this time, we found that the password of admin was changed to ccccc, while the password of the user admin'# we registered was not changed.
Cause of the vulnerability
1. Special characters such as ' and # are allowed when registering a user.
2. In the source code of the password modification page, it is found that there is an obvious injection vulnerability
$sql = "UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' ";
When we log in to the account admin'# and change the password, this SQL statement becomes as follows. #Comments out the following code, so the password of user admin is changed to ccccc
$sql = "UPDATE users SET PASSWORD='$pass' where username='admin'#' and password='$curr_pass' ";
Original link: https://blog.csdn.net/qq_44159028/article/details/114325805