2024-07-12
한어Русский языкEnglishFrançaisIndonesianSanskrit日本語DeutschPortuguêsΕλληνικάespañolItalianoSuomalainenLatina
Headerpwn is a fuzz testing tool for server responses and HTTP Headers. Researchers can use this tool to find network anomalies and analyze how servers respond to different HTTP Headers.

The current version of headerpwn supports the following features:
1. Server security and anomaly detection;
2. HTTP Header detection;
3. Test how the server responds to different HTTP Headers;
4. Report output and command line display;
5. User-friendly and easy to operate;
Go
Since this tool is developed based on the Go language, we first need to install and configure the latest version of the Go environment on the local device.
Next, researchers can download and install headerpwn directly using the following commands:
go install github.com/devanshbatham/[email protected]
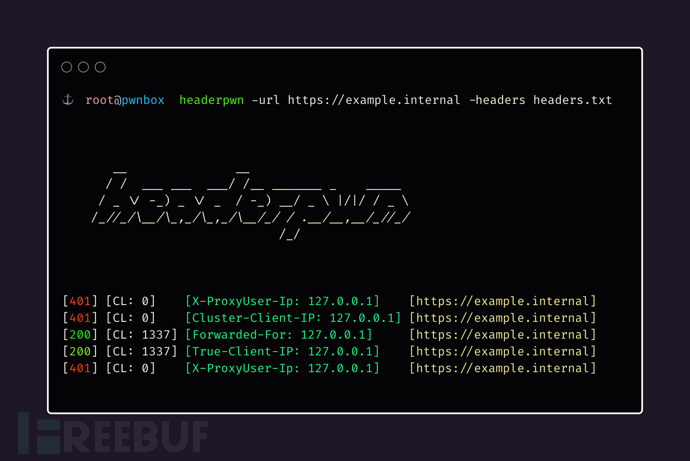
Headerpwn can help researchers test various headers on the target URL and analyze its response information. The tool is used as follows:
1. Use the -url parameter to provide headerpwn with the target URL to be tested;
2. Create a header list file containing the target URL to be tested, with each header on a separate line. Use the -headers parameter to specify the list file path to headerpwn.
The usage examples are as follows:
headerpwn -url https://example.com -headers my_headers.txt
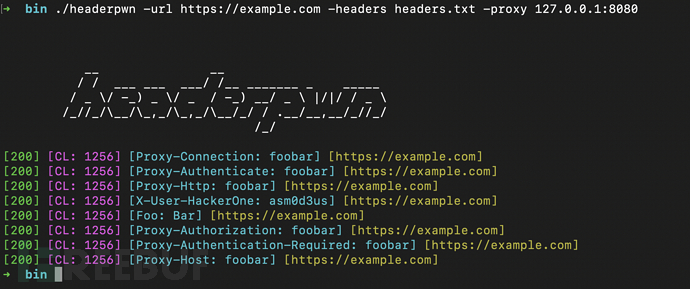
The data format of my_headers.txt is as follows:
Proxy-Authenticate: foobar Proxy-Authentication-Required: foobar Proxy-Authorization: foobar Proxy-Connection: foobar Proxy-Host: foobar Proxy-Http: foobar
We can follow the steps below to proxy the request with Burp Suite:
1. In Burp Suite, go to the Proxy tab.
2. In the "Proxy Listener" page, select the configured listener 127.0.0.1:8080;
3. Click the "Import/Export CA Certificate" button;
4. In the certificate window, click "Export Certificate" and save the certificate file (for example, burp.der);
1. Install the exported certificate as a trusted certificate on your system. The specific operation depends on your operating system;
2. On Windows, you can double-click the .cer file and follow the prompts to install it in the Trusted Root Certification Authorities store;
3. On macOS, you can double-click the .cer file and add it to the Keychain Access application in the System keychain;
4. On Linux, you may need to copy the certificate to a trusted certificate location and configure the system to trust it;
Next, run the following command:
headerpwn -url https://example.com -headers my_headers.txt -proxy 127.0.0.1:8080
The development and release of this project followsMITOpen source license agreement.
headerpwn:【GitHub Portal】